SCP
Security Convergence Platform
SCP
AI-Integrated Cyber Threat Monitoring and Analysis Platform
Security Convergence Platform unifies network security data onto a single platform. This advanced analysis tool finds hidden threats and compromised devices & networks — automatically alerting staff according to the security threat level. The platform gives organizations and enterprises the power to track, analyze, and proactively resolve issues across IT and OT assets.
BENEFITS
SCP
Benefits
Manage Security Systems from a Single Platform
Scalable and Seamlessly Integrates with Existing Systems
Lower Operational Costs Via Automation
Improved Threat Detection and Prevention
Real-time Monitoring with Faster Responses
Enhanced Data Analysis for Patterns and Anomalies
Predictive Analytics to Prevent Security Threats Before They Occur
Automated Responses that Mitigate Security Risks
AI-led Automation that Frees up Resources
Improved Compliance with Security Standards and Regulations
SCP
Powering Security Convergence on The Platform
SCP
Key Features
Threat Detection and Notifications
Centralized Incident Management
Threat Intelligence
Security Alerting
Real-time Notifications
Data Collection and Management
Event Correlation and Analytics
Incident Management
Risk Assessments
Dashboard and Reporting
SCP
Core Capabilities
SCP provides organizations and governments the power to protect their systems with a centralized cybersecurity monitoring and management platform.
To go even further, SCP supports other cybersecurity products, such as Firewalls, IDS/IPS, WAF, Antivirus software, AD, Secure Email Gateway, etc..
01
Threat Intelligence Management
- Imports both open-source Cyber Threat Intelligence and commercial CTI feeds.
- Automatically feeds discovered suspicious IPs to the Threat Intelligence module.
- Provides joint defense with threat information shared with every module.
- Performs defensive actions simultaneously and seamlessly with every module.
02
Threat Assessment
- Enables admins with alert notifications that combine data from NetProbe, NetTrap, HMD, and system logs.
- Classifies alerts into various threat alarms according to level of severity.
- Notifies admins with the necessary protective actions needed.
03
Cyber Threat Prevention
- Defends against global and targeted threat attacks.
- Blocks the spread of vulnerability infections and uses machine learning for detection.
- Collects endpoint host system information to determine whether it meets Government Configuration Baseline.
- Identifies software vulnerabilities and issues alerts.
- Matches threat conditions to detect malicious software and activities with machine learning and digital forensics.
04
Regular Endpoint Health Checks
- Enables admins to review CPU, memory, disk usages and investigate abnormal files, processes, network connections, and resource usage of each endpoint.
- Provides key metrics such as network traffic, usage time, unknown network services, and DNS query failure rates.
05
Visualized Data & Charts
- Manages sources of cyber threats IPs on a graphical interface.
- Provides admins with data such as time of the attack, global locale of the attack, and which protocol was targeted.
- Presents statistical information of various attacks, threats, and alarms with graphs and charts.
06
Network Asset Management
- Enables users to map out and monitor internal network threats and cut them off.
- Maintains a complete list of network equipment and network topology.
- Provides information security module with tracking, reviewing, reporting, and alert capabilities.
- Allows admins to mark equipment location with a floor plan.
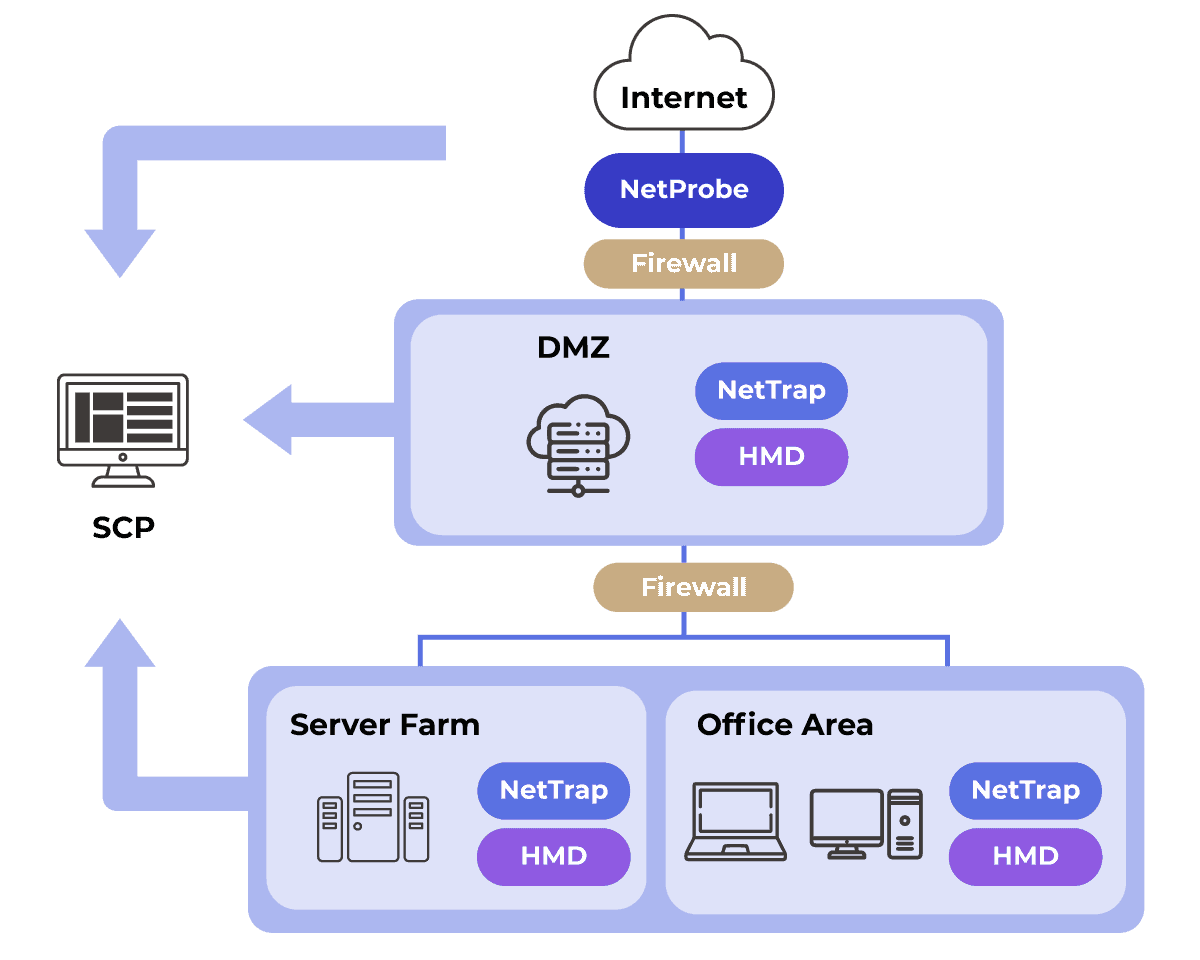
SCP
Architecture
- Leverages Gorilla’s network products into one total solutions for seamless, layered security.
- Provides IT staff with a centralized monitoring and management platform.
- Scalable from small setups to multi-site networks and supports other cybersecurity products.

Discover why so many government agencies and enterprises chose Gorilla’s Security Converge Platform to manage and protect their systems from internal and external threats with superior AI.
Are You Ready to Unlock Superior Cybersecurity Management with Gorilla?
Speak to our team of experts now.