HMD
Host-based Malware Detection
HMD
Powerful AI for Superior Endpoint Protection That Fights Malware
Host-based Malware Detection (HMD) is a malware defense solution from Gorilla Security Convergence that leverages edge AI to offer innovative network protection. HMD is also an Endpoint Detection and Response (EDR) solution which is an integrated endpoint security solution that combines real-time continuous monitoring and collection of endpoint data with rules-based automated response and analysis capabilities.
HMD
Benefits
Real-time Threat Detection
Enhanced Anomaly Detection
Improved Software Vulnerability Identification
Rapid Response to Malware Threats
Reduced False Positives
Continuous Monitoring of Endpoint Health
Automatic Updates for Evolving Threats
Minimized Manual Intervention
Enhanced Protection Against Advanced Persistent Threats
Comprehensive Endpoint Security Solution
HMD
Key Features
Advanced Anomaly Detection
Endpoint Protection Enhanced with AI
Multi-faceted Threat Detection
Patternless AI-based Malware Detection Engine
Automatically Detects Malicious Programs and Files
Removes Malware Threats from Systems
Automatic Incident Responses that Isolate or Shutdown Compromised Hosts
AI Algorithms and Digital Forensics
Alerts and Notifications for Endpoint Risks
HMD
Core Capabilities
Utilizing an AI-powered malware detection engine, HMD constantly checks endpoint health, identifies unusual activity, and notifies you about software vulnerabilities, and prevents advanced persistent threats, traces their origins, and responds effectively to provide complete endpoint security.
01
Threat Detection
- Utilizes AI-assisted machine learning to automatically detect suspicious programs and reports results.
- Monitors if an unknown process is present in memory and determines if files have been damaged or compromised.
- Finds and reports problems with endpoint hosts.
02
Advanced Persistent Threat Protection
- Detects various known APT signatures to prevent endpoint intrusions.
- Detects hidden, packed, corrupt, and fake files.
- Detects fake and invalid digital signatures.
03
Weakness Detection
- Analyzes the health status of each host and tracks high-risk vulnerabilities.
- Finds weaknesses and vulnerabilities at the application level and reports the detection results.
- Compliant with the Government Configuration Baseline (GCB).
04
Centralized Reporting Module
- Centralizes the management of threats and resources, and deals with them according to specific priorities.
- Utilizes Gorilla’s Security Convergence Platform monitoring module.
- Categorizes various threats and tiers them with necessary responses.
05
Incident Response
- Detects and reports threats to administrators.
- Automatically responds with actions such as disconnecting networks, shutting down compromised endpoints or performs Yara scans.
- Performs scans and sends reports to admins enabling them respond to security incidents effectively.
06
Automated Program Delivery
- Enables large-scale deployment to be carried out through an Activity Directory.
- Admins do not need to manually manage the dispatch list.
- Reduces complexity and ensures every endpoint is followed rigorously.
HMD
Architecture
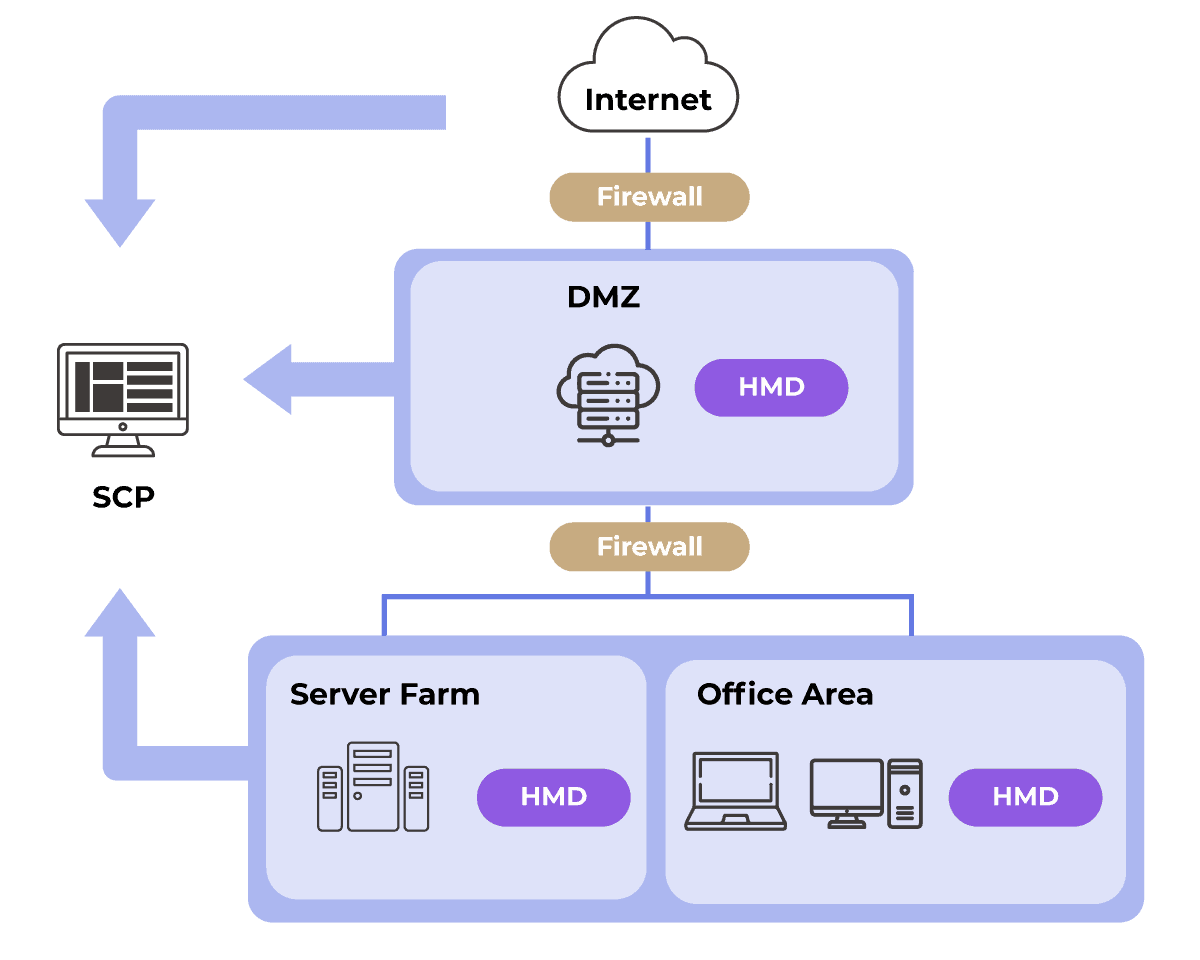

Discover why so many government agencies and enterprises chose HMDto protect their internal systems from malware with superior AI.
Are You Ready to Unlock Superior Protection with HMD?
Speak to our team of experts now.